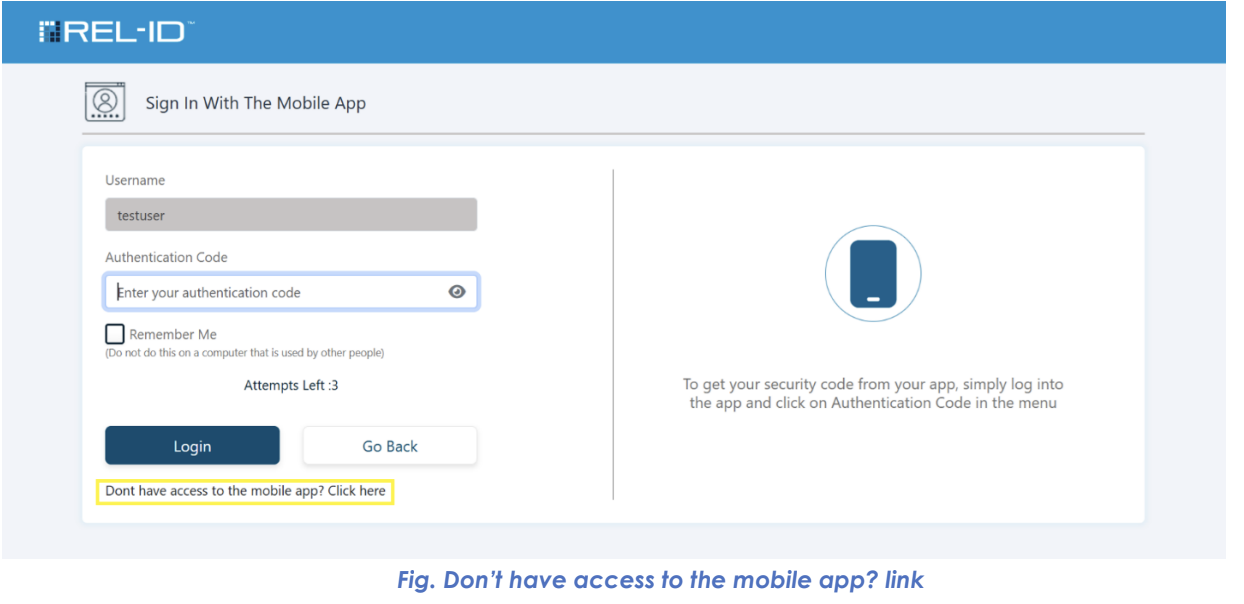
Don’t have access to the mobile app ?
🎯 Purpose
Provides recovery assistance for users who cannot access their REL-ID mobile application to retrieve the required authentication code for login.
📍 Context and Availability
- Trigger Scenario: User needs authentication code from mobile app but cannot access it
- Screen Location: Authentication code entry screen
- Link Text: "Don't have access to the mobile app? Click here"
- User Situation: Mobile device unavailable, app not working, or connectivity issues
🔄 Mobile App Access Issues
📱 Common Scenarios Requiring Recovery
| Scenario | Description | User Impact |
|---|---|---|
| Device Lost/Stolen | Mobile device no longer available | Cannot generate authentication codes |
| App Malfunction | REL-ID app not working properly | Cannot access authentication codes |
| Device Damage | Mobile device physically damaged | Cannot operate mobile application |
| Battery Dead | Mobile device without power | Cannot access authentication codes |
| Network Issues | Connectivity problems with mobile device | May affect some authentication methods |
| App Deletion | REL-ID app accidentally removed | Cannot generate authentication codes |
🖥️ Recovery Link Interface
📱 Link Presentation
The recovery link is presented contextually when users are expected to enter a mobile authentication code:
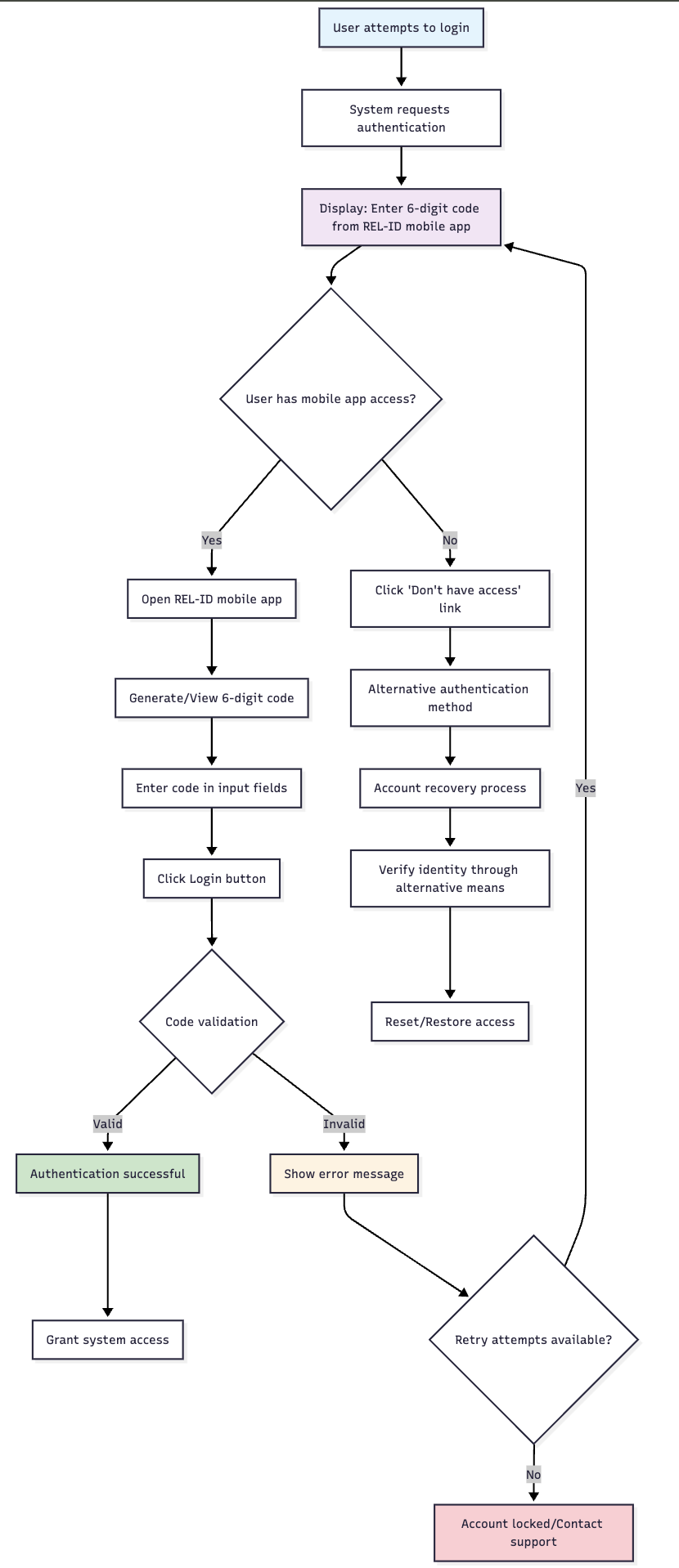
🔄 Recovery Process Flow
🆘 Recovery Initiation
- Link Click: User clicks "Don't have access to the mobile app?" link
- Context Capture: System captures current authentication state
- Recovery Redirect: User redirected to appropriate recovery mechanism
- State Preservation: Authentication progress maintained for recovery
🛡️ Recovery Path Options
Based on system configuration and user profile, several recovery paths may be available:
- Alternative Factors: Other registered authentication methods
- IDV Process: Identity verification through AR-IDV module
- Account Recovery: Full account recovery workflow
- Support Contact: Direct assistance from support team
🎯 User Experience
📱 Contextual Help
- Timely Assistance: Help available exactly when needed
- Clear Messaging: Link text clearly describes the issue
- Immediate Access: Single click to access recovery options
- Progress Preservation: Authentication state maintained during recovery
🔄 Alternative Authentication
- Factor Switching: Access to other registered authentication methods
- Backup Options: Use of alternative authentication factors
- Recovery Guidance: Clear instructions for alternative methods
- Flexibility: Multiple paths to complete authentication
⚠️ Important Considerations
🔒 Security Maintenance
- Identity Verification: Recovery maintains security standards
- Authentication Requirements: Alternative methods still require proper verification
- Session Security: Recovery process maintains session integrity
- Audit Trail: All recovery actions properly logged
🎯 User Guidance
- Clear Options: Available recovery methods clearly presented
- Step-by-Step: Guided process through recovery options
- Support Information: Contact details for additional assistance
- Progress Indicators: Users understand their position in recovery process
Updated 15 days ago
