Account Recovery Link Action
🎯 Purpose
Serves as the central routing mechanism that directs users from various account recovery links to the appropriate recovery system, providing flexibility for both default REL-ID recovery and custom enterprise solutions.
🏗️ Recovery Link Architecture
The Account Recovery Link Action system acts as a configurable gateway that can route users to different recovery implementations based on organizational needs and system configuration.
🔄 Recovery Link Sources
📍 Recovery Link Locations
Account recovery links are strategically placed throughout the authentication system:
- Pre-login Recovery: "Don't have access to the mobile app" and "Forgot Password" links
- Partial-login Recovery: "Don't have access to the mobile app", "Can't access Email", "Can't access SMS" links
- Custom Integration Points: Enterprise-specific recovery entry points
⚙️ Configuration and Routing
🔧 System Configuration
The recovery link destination is controlled through system configuration:
- Configuration Location: System administration settings
- Default Behavior: Routes to REL-ID Browser-based Account Recovery IDV module
- Custom Configuration: Can be changed to route to customer's existing IDV system
- Flexibility: Supports both out-of-the-box and custom recovery solutions
📊 Routing Options
| Configuration | Destination | Use Case |
|---|---|---|
| Default REL-ID | Browser-based Account Recovery IDV (AR-IDV) | Standard REL-ID recovery process |
| Custom Enterprise | Customer's existing IDV system | Enterprise integration with existing systems |
| Hybrid Approach | Mixed routing based on recovery type | Different recovery methods for different scenarios |
🔄 Default Recovery Flow
🎯 REL-ID AR-IDV Module
When using the default configuration, recovery links route to the REL-ID Browser-based Account Recovery IDV module:
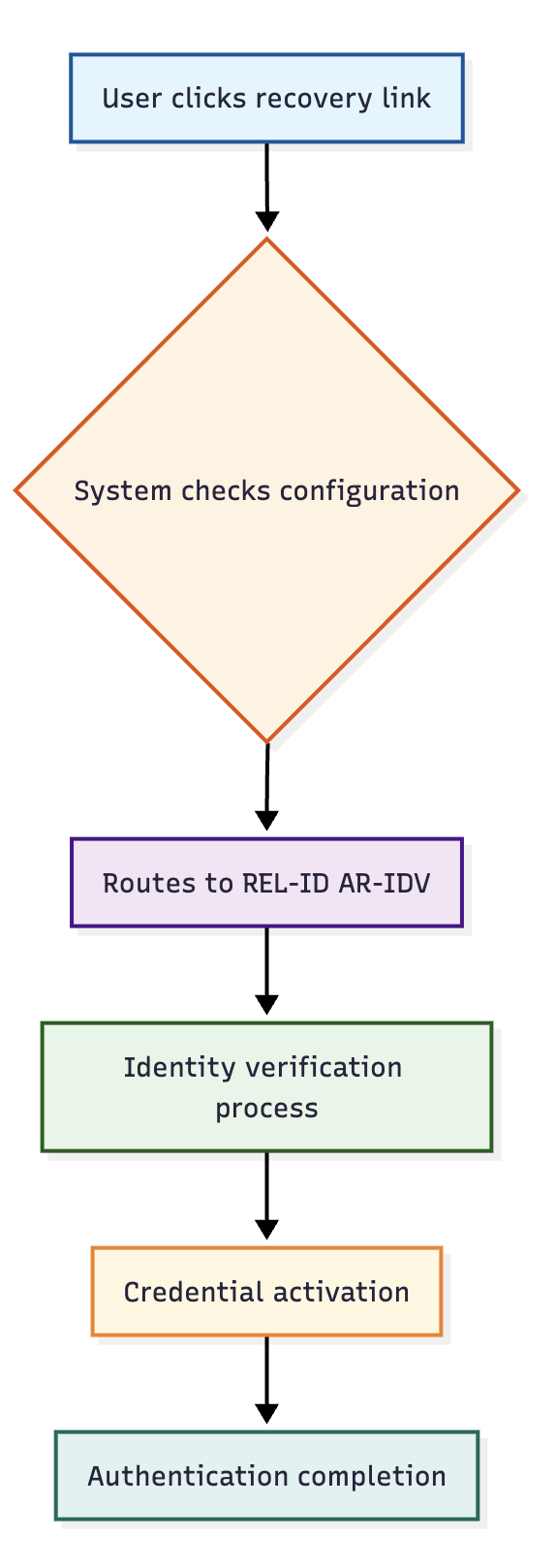
🛡️ Default Process Benefits
- Integrated Security: Seamless integration with REL-ID security model
- Consistent Experience: Uniform recovery experience across all scenarios
- Comprehensive IDV: Multiple identity verification methods available
- Audit Integration: Complete logging within REL-ID system
🏢 Enterprise Custom Integration
🔧 Custom IDV System Integration
Enterprises can configure recovery links to route to their existing identity verification systems:
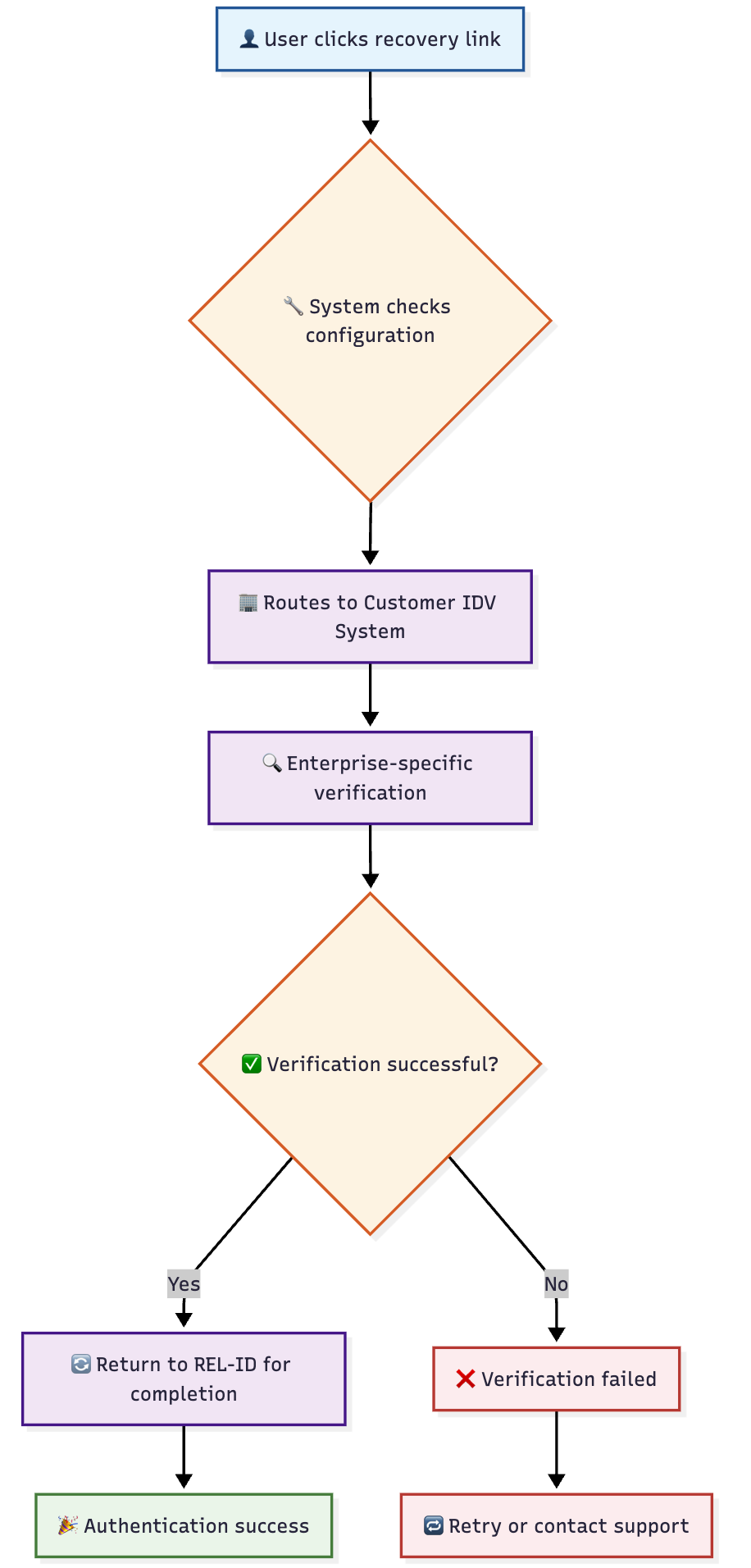
📊 Enterprise Integration Benefits
| Benefit | Description | Value |
|---|---|---|
| Existing Infrastructure | Leverages current IDV investments | Cost efficiency |
| Consistent Branding | Maintains enterprise user experience | Brand consistency |
| Compliance Integration | Works with existing compliance systems | Regulatory alignment |
| Custom Workflows | Supports specific business processes | Operational alignment |
🔗 Integration Architecture
🛠️ Technical Integration Points
- URL Configuration: Simple URL redirect configuration
- Parameter Passing: Context information passed to custom systems
- Return Integration: Secure return path back to REL-ID system
- State Management: Authentication state preserved across systems
📊 Integration Parameters
Information passed to custom IDV systems:
- User Identifier: REL-ID username or user ID
- Recovery Context: Type of recovery being attempted
- Authentication State: Current authentication progress
- Session Token: Secure session identifier
- Return URL: Secure return path to REL-ID system
🎯 Configuration Management
⚙️ Configuration Process
- System Access: Administrator accesses system configuration
- URL Configuration: Set custom IDV system URL
- Parameter Setup: Configure information sharing parameters
- Return Path: Establish secure return integration
- Testing: Validate configuration in test environment
- Deployment: Activate configuration in production
🔒 Security Considerations
- Secure Communication: All integrations use encrypted channels
- Parameter Validation: Information passed is properly validated
- Return Security: Return path includes security token validation
- Audit Trail: All routing decisions logged for security monitoring
🔄 Recovery Flow Variations
📊 Flow Comparison
| Aspect | REL-ID Default | Custom Enterprise |
|---|---|---|
| IDV Methods | REL-ID standard methods | Enterprise-specific methods |
| User Experience | REL-ID interface | Enterprise-branded interface |
| Integration | Fully integrated | Hybrid integration |
| Customization | Standard options | Full customization |
| Maintenance | REL-ID managed | Enterprise managed |
⚠️ Important Implementation Notes
🔧 Configuration Requirements
- URL Validation: Custom URLs must be properly validated and secure
- Return Integration: Secure return path must be properly implemented
- Parameter Security: Information sharing must follow security protocols
- Testing Requirements: Thorough testing required before production deployment
🛡️ Security Requirements
- HTTPS Mandatory: All custom integrations must use secure protocols
- Token Validation: Return paths must include proper token validation
- Audit Logging: All recovery routing must be properly logged
- Access Control: Custom systems must implement proper access controls
Updated 15 days ago
