Forgot Password
🎯 Purpose
Assists users who have forgotten the password they set up for account access, providing a secure method to regain authentication capability.
📍 Context and Availability
- Trigger Scenario: User cannot remember their authentication password
- Screen Location: Password entry screen
- Link Text: "Forgot your password? Click here"
- User Situation: Password forgotten, account lockout due to failed attempts, or password confusion
🖥️ Password Recovery Interface
🔒 Link Presentation
The password recovery link appears contextually when users are prompted to enter their password:
🔄 Password Recovery Scenarios
🚨 Common Password Issues
| Issue | Description | Recovery Need |
|---|---|---|
| Forgotten Password | User cannot remember password | Password reset process |
| Account Lockout | Too many failed password attempts | Account unlock and password reset |
| Password Expired | Password beyond expiration period | Password update requirement |
| Policy Changes | New password policies not met | Password compliance update |
| Multiple Passwords | Confusion between different passwords | Password clarification or reset |
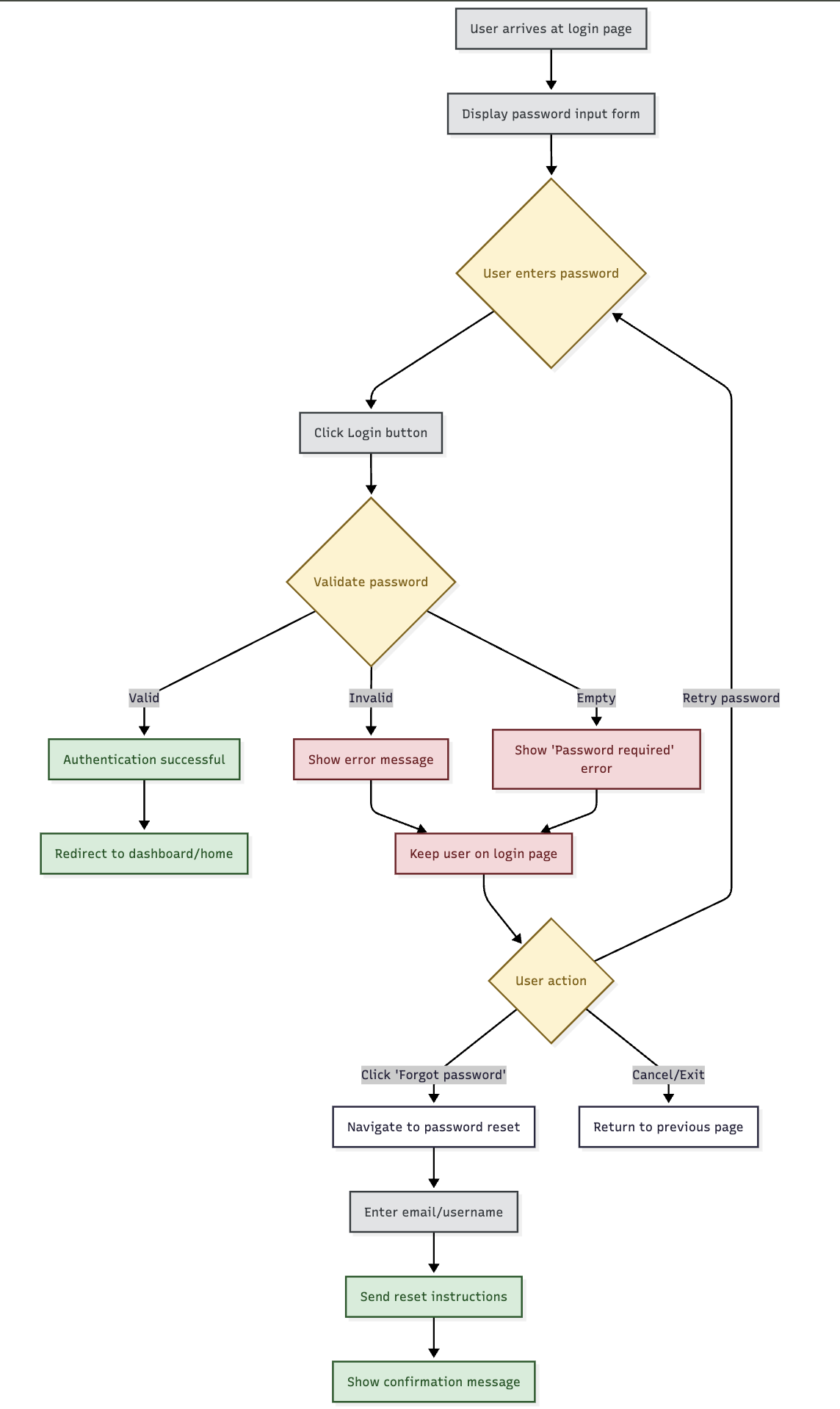
🔄 Recovery Process Flow
🆘 Password Recovery Initiation
- Link Click: User clicks "Forgot your password? Click here" link
- Context Capture: System records current authentication attempt
- Recovery Routing: User directed to appropriate recovery mechanism
- Identity Verification: Recovery process begins with identity confirmation
🛡️ Password Recovery Methods
Based on system configuration and user profile:
- Security Questions: Knowledge-based authentication
- Email Verification: Password reset via registered email
- SMS Verification: Password reset via registered mobile number
- IDV Process: Full identity verification through AR-IDV
- Administrative Reset: Support-assisted password reset
🔒 Security Considerations
🛡️ Recovery Security Measures
- Identity Verification Required: All password recovery requires identity confirmation
- Multi-Factor Verification: Recovery uses alternative authentication methods
- Secure Channels: Recovery communications use encrypted channels
- Time Limitations: Recovery tokens have limited validity periods
📊 Recovery Verification Methods
| Method | Verification Type | Security Level |
|---|---|---|
| Email OTP | Code sent to registered email | Medium |
| SMS OTP | Code sent to registered mobile | Medium |
| Security Q&A | Knowledge-based questions | Medium |
| Full IDV | Complete identity verification | High |
| Administrative | Support-verified recovery | High |
🎯 User Experience
🔄 Recovery Process Flow
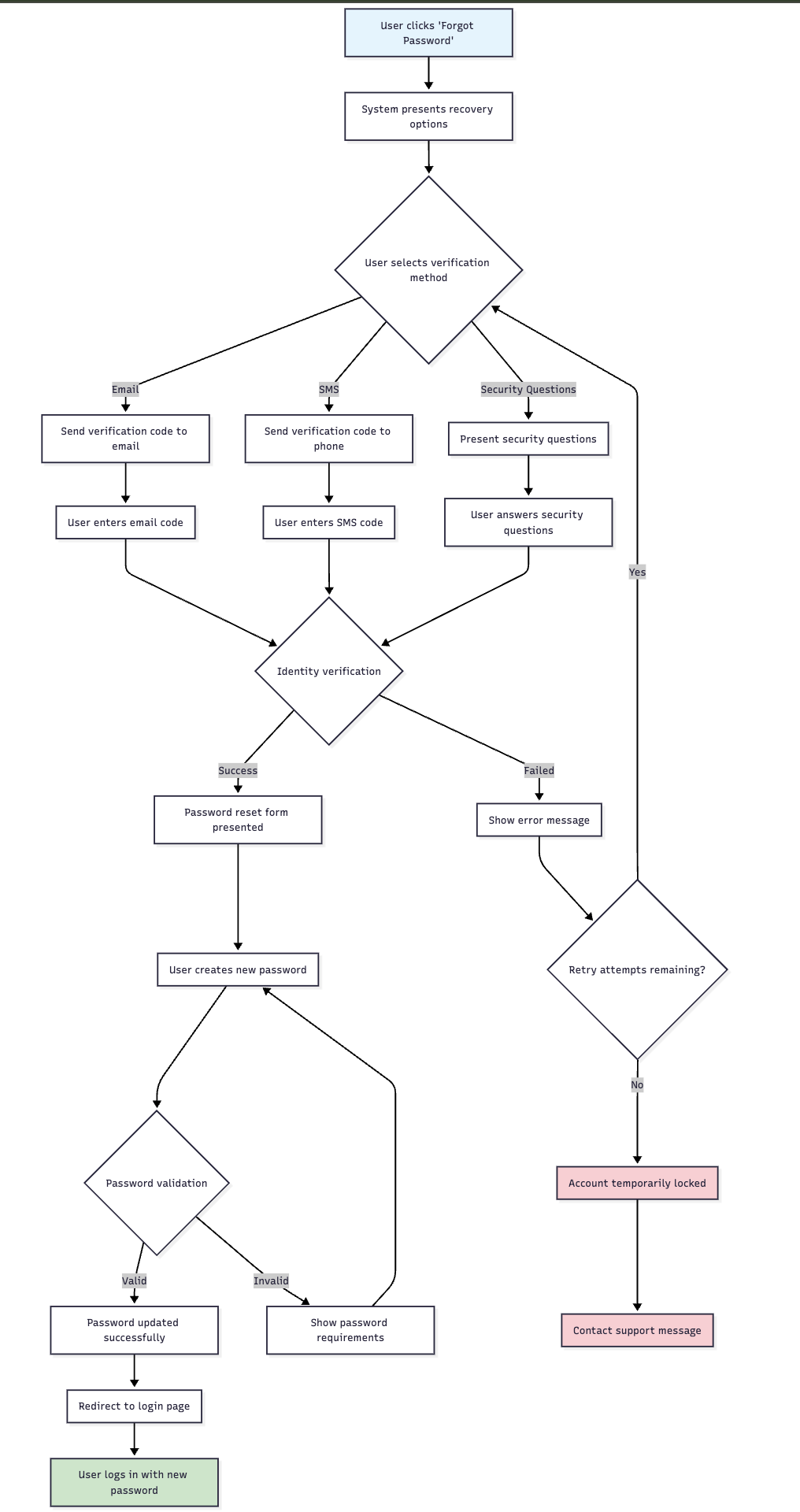
📱 User-Friendly Features
- Multiple Options: Various recovery methods available
- Clear Guidance: Step-by-step recovery instructions
- Progress Tracking: Users understand recovery progress
- Immediate Use: New password immediately active
⚠️ Important Recovery Notes
🔐 Security Requirements
- Verification Mandatory: Password recovery always requires identity verification
- Secure Process: All recovery steps maintain security standards
- Audit Trail: Complete logging of password recovery activities
- Policy Compliance: New passwords must meet current policy requirements
🎯 Post-Recovery Actions
- Immediate Authentication: New password immediately usable
- Security Confirmation: User confirmation of successful password change
- Additional Factors: Second-factor authentication still required
- Account Security: Guidance on maintaining account security
Updated 15 days ago
