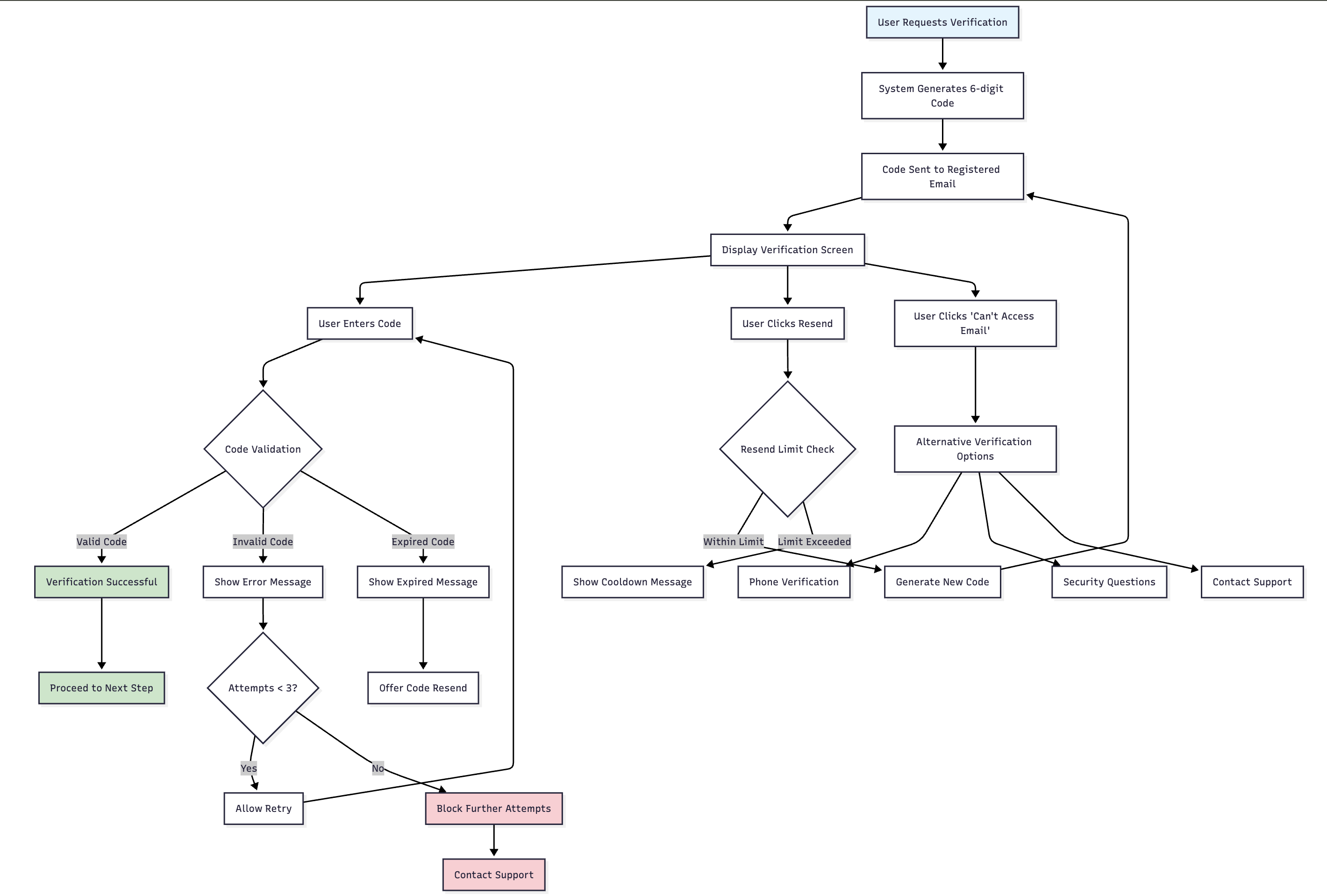
Can’t access Email ?
🎯 Purpose
Provides recovery assistance for users who cannot access their email to retrieve the verification code required for email-based second-factor authentication.
📍 Context and Availability
- Trigger Scenario: User cannot access email account to retrieve OTP code
- Screen Location: Email OTP verification screen
- Link Text: "Can't access Email? Click here"
- Authentication State: First factor completed, email OTP required
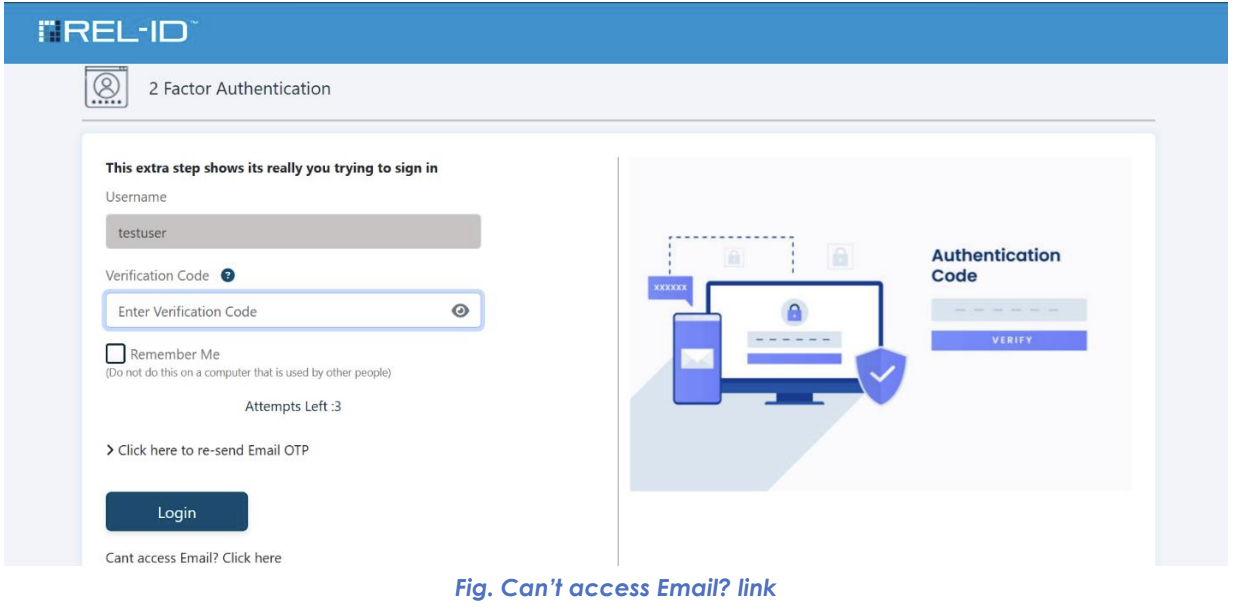
🖥️ Email Access Recovery Interface
📧 Recovery Link Presentation
📨 Email Access Issues
🚨 Common Email Access Problems
| Issue | Description | User Impact |
|---|---|---|
| Password Forgotten | User cannot log into email account | Cannot retrieve verification codes |
| Account Locked | Email account temporarily locked | No access to email messages |
| Service Outage | Email provider experiencing outages | Email delivery or access delayed |
| Mobile Email Issues | Problems with mobile email apps | Cannot access email on mobile device |
| Spam Filtering | Verification emails filtered as spam | Codes not visible in main inbox |
| Email Change | Email address changed but not updated | Codes sent to old, inaccessible email |
| Corporate Restrictions | Work email blocked or restricted | Cannot access emails outside work hours |
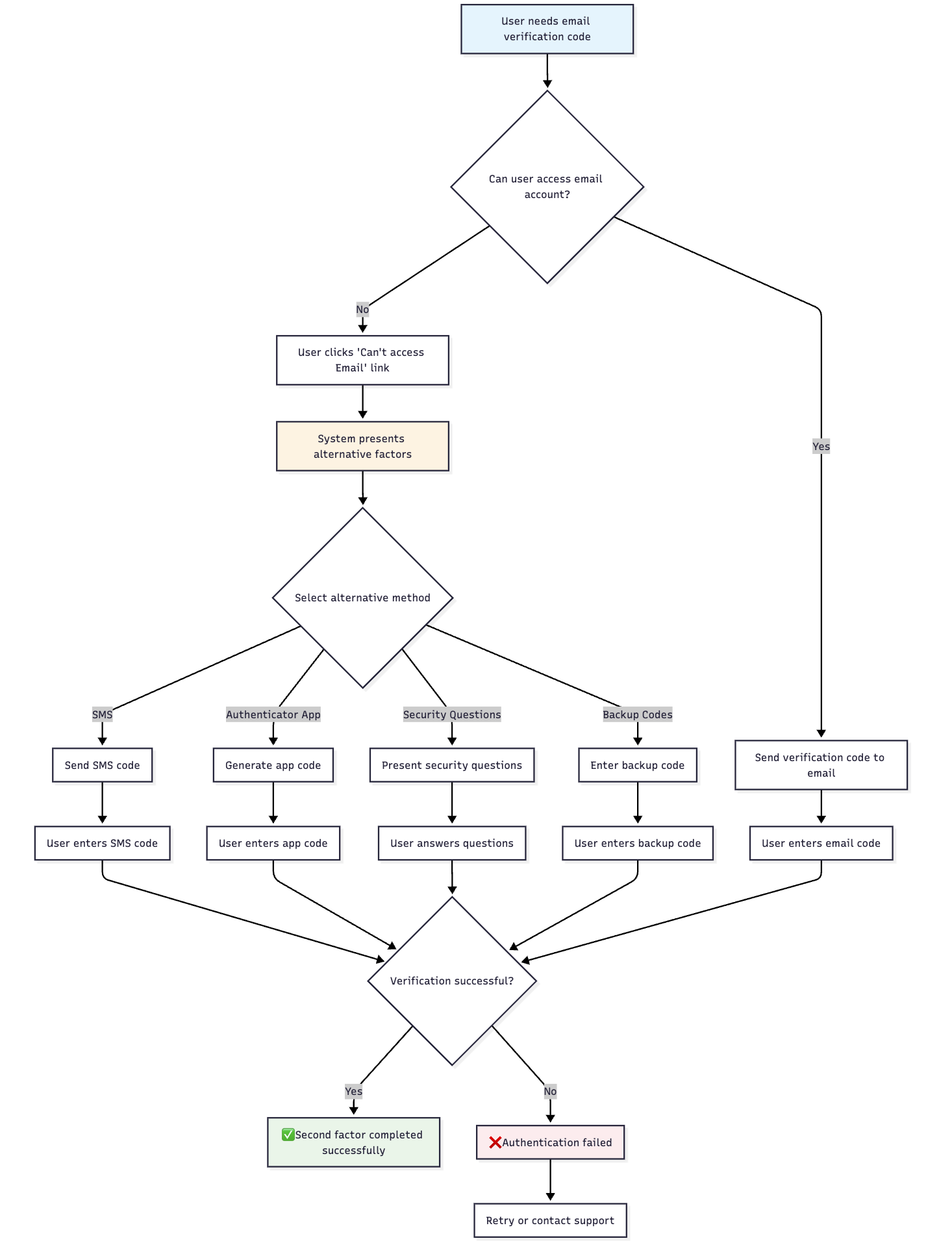
🔄 Email Recovery Process Flow
🆘 Email Access Recovery
- Recovery Link Click: User clicks "Can't access Email?" recovery link
- State Preservation: First factor authentication maintained
- Alternative Presentation: System offers alternative second factor methods
- Method Selection: User chooses from available alternatives
- Factor Completion: Alternative authentication method completed
- Authentication Success: Access granted after successful alternative factor
🔄 Alternative Second Factor Options
Available alternatives based on user configuration:
- SMS OTP: Switch to SMS-based verification codes
- Mobile App: Use push notification or TOTP from mobile app
- Security Questions: Knowledge-based authentication
- Administrative Recovery: Support-assisted verification
- Full IDV: Complete identity verification process
📊 Email Recovery Scenarios
| Recovery Method | Availability Requirement | Security Level |
|---|---|---|
| SMS OTP | Registered mobile number | Medium |
| Push Notification | Active REL-ID mobile app | High |
| Time-based OTP | REL-ID mobile app access | High |
| Security Q&A | Previously configured questions | Medium |
| Full IDV | System IDV configuration | Very High |
🎯 User Experience
📧 Email Recovery Flow
📱 Recovery Interface Features
- Clear Problem Statement: Recovery link clearly describes email access issue
- Immediate Alternatives: Quick access to other authentication methods
- State Continuity: First factor authentication preserved
- Multiple Options: Various alternative methods available
🛡️ Security Considerations
🔒 Recovery Security
- Equivalent Protection: Alternative factors provide similar security levels
- Identity Verification: All alternatives require proper user verification
- Audit Logging: Email recovery attempts properly logged
- Session Security: Authentication session integrity maintained
📊 Security Validation
- Factor Verification: Alternative factors properly validated
- User Control: Recovery requires user control of alternative factors
- Time Limits: Recovery processes have appropriate time constraints
- Abuse Prevention: Rate limiting prevents recovery abuse
⚠️ Important Recovery Notes
📧 Email Access Tips
- Spam Check: Users guided to check spam/junk folders
- Service Status: Information about checking email service status
- Alternative Access: Suggestions for alternative email access methods
- Update Guidance: Instructions for updating email address if needed
🔄 Post-Recovery Actions
- Email Update: Guidance for updating email address if permanently inaccessible
- Factor Review: Recommendation to review and diversify authentication factors
- Support Contact: Information for persistent email access issues
- Account Security: Guidance on maintaining secure email access
Updated 15 days ago
