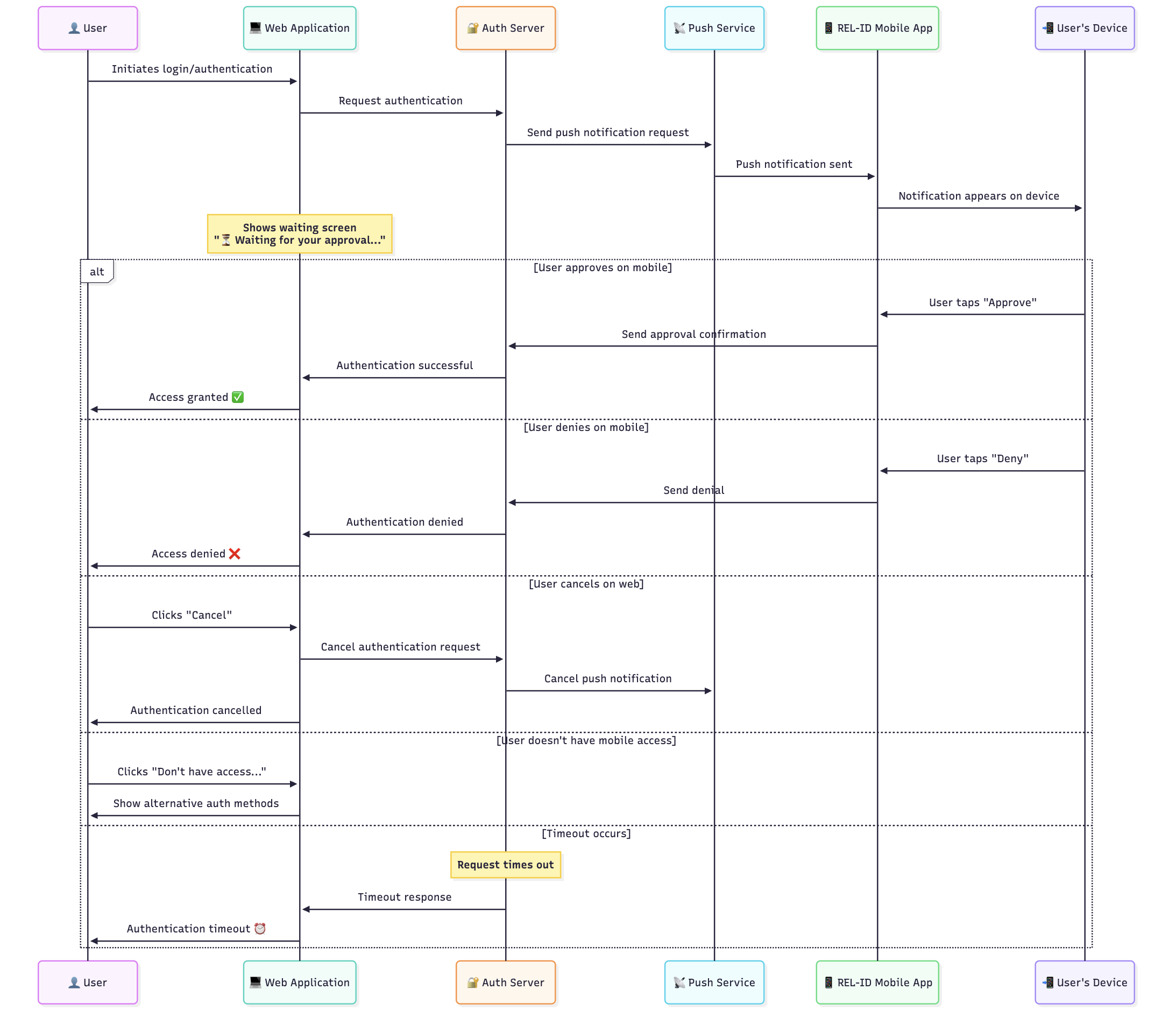
Don’t have access to the mobile app ?
🎯 Purpose
Provides recovery assistance for users who cannot access their REL-ID mobile application to approve push notifications required for second-factor authentication completion.
📍 Context and Availability
- Trigger Scenario: User cannot approve push notification sent to mobile app
- Screen Location: Push notification waiting screen
- Link Text: "Don't have access to the mobile app? Click here"
- Authentication State: First factor completed, push notification sent
🖥️ Push Notification Recovery Interface
🔔 Recovery Link Presentation
📱 Mobile App Access Issues in Partial-login
🚨 Common Scenarios
| Issue | Description | User Impact |
|---|---|---|
| Device Unavailable | Mobile device lost, stolen, or damaged | Cannot receive or approve push notifications |
| App Malfunction | REL-ID app not responding | Cannot interact with push notifications |
| Connectivity Issues | Mobile device offline or poor connection | Push notifications not delivered |
| Notification Blocked | Push notifications disabled or blocked | Cannot see authentication requests |
| Battery Dead | Mobile device without power | Cannot access mobile application |
| App Deleted | REL-ID application removed from device | No push notification capability |
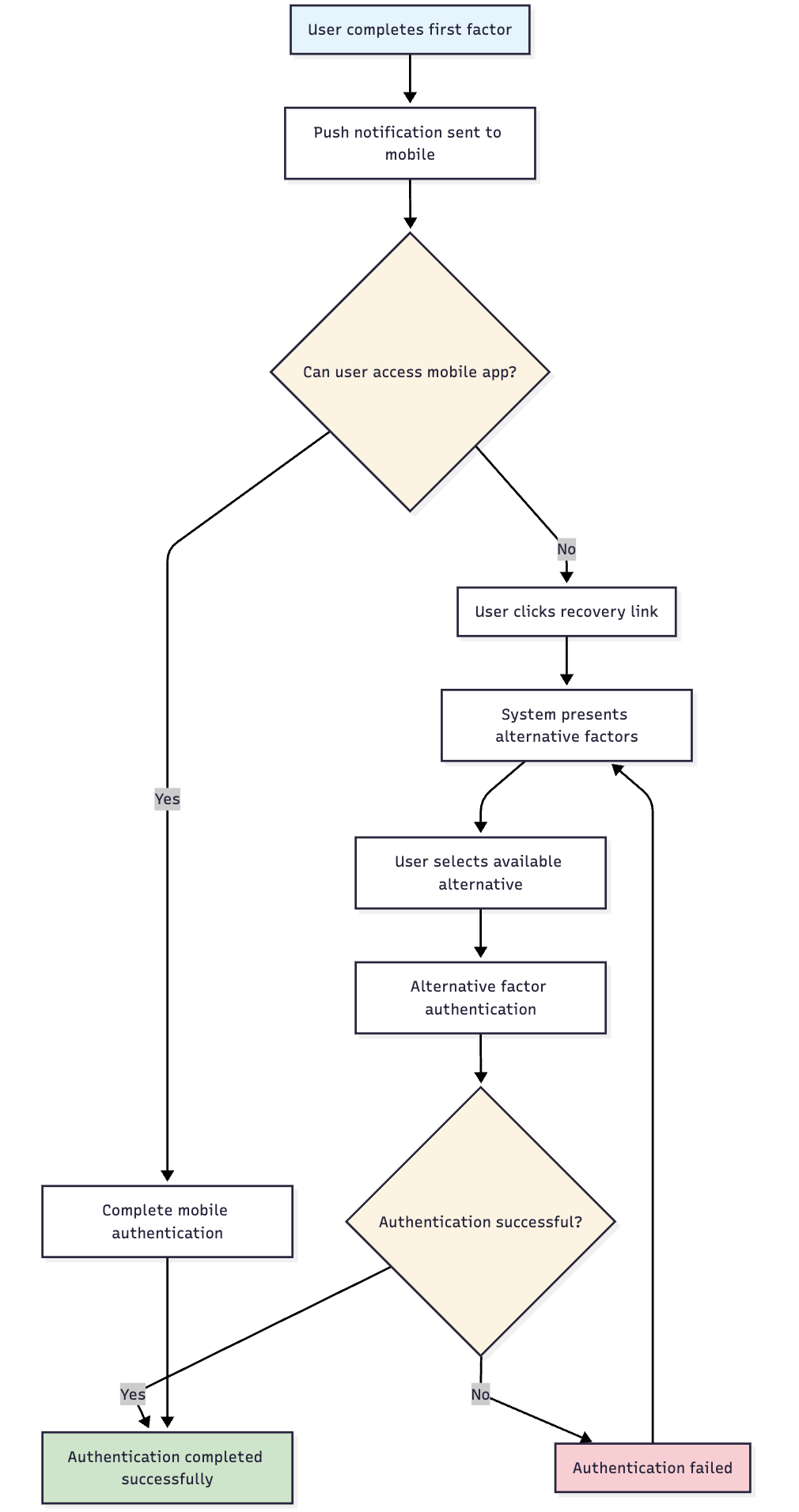
🔄 Recovery Process Flow
🆘 Push Notification Recovery
- Recovery Link Click: User clicks mobile app access recovery link
- Context Preservation: System maintains first factor authentication state
- Alternative Methods: User presented with alternative second factor options
- Method Selection: User chooses available alternative authentication method
- Factor Completion: Alternative second factor authentication completed
- Authentication Success: User gains access after completing alternative factor
🔄 Alternative Second Factor Options
Available alternatives depend on user profile and system configuration:
- Time-based OTP: Use TOTP codes from mobile app (if app accessible for codes only)
- Email OTP: Switch to email-based one-time password
- SMS OTP: Switch to SMS-based one-time password
- Password Challenge: Additional password verification
- Full Recovery: Complete identity verification process
🎯 User Experience
📱 Contextual Recovery
- Immediate Help: Recovery option available during push notification wait
- State Preservation: First factor authentication maintained during recovery
- Clear Options: Alternative methods clearly presented
- Smooth Transition: Seamless switch to alternative authentication methods
🔄 Recovery Flow Diagram
⚠️ Important Considerations
🔒 Security Maintenance
- Factor Equivalence: Alternative factors provide equivalent security
- Authentication State: First factor authentication preserved
- Audit Trail: Recovery actions properly logged
- Session Integrity: Authentication session maintained throughout recovery
🎯 Recovery Efficiency
- Quick Access: Immediate access to recovery options
- Multiple Alternatives: Several recovery paths available
- User Choice: Users can select preferred alternative method
- Completion Focus: Recovery designed for authentication completion
Updated 15 days ago
